Encryption Algorithms:-
Their are Symmetric Block Cipher Algorithms- DES (Data Encryption Standard)
- 3DES (Triple DES)
- AES (Advanced Encryption Standard)
Data Encryption Standard (DES):-
History:-
working:-
AES (ADVANCED ENCRYPTION ALGORITHM):-
AES is a block cipher with a block length of 128 bits.
AES allows for three different key lengths: 128, 192, or 256 bits.
Most of our discussion will assume that the key length is 128 bits.
Encryption consists of
- 10 rounds of processing for 128-bit keys,
- 12 rounds for 192-bit keys,
- 14 rounds for 256-bit keys.
• To appreciate the processing steps used in a single round, it is best to think of a 128-bit block as consisting of a 4 × 4 matrix of bytes, arranged as follows:
Therefore, the first four bytes of a
128-bit input block occupy the first column in the 4 × 4 matrix of bytes. The
next four bytes occupy the second column, and so on.
The 4×4 matrix of bytes shown above is referred to as the state array in AES.
The algorithm begins with an Add round key stage followed by 9 rounds of four stages and a tenth round of three stages.
This applies for both encryption and decryption with the exception that each stage of a round the decryption algorithm is the inverse of its counterpart in the encryption algorithm.
The four stages are as follows: 1. Substitute bytes 2. Shift rows 3. Mix Columns 4. Add
Round Key.
Substitute Bytes:-
•This stage (known as Sub Bytes) is simply a table lookup using a 16 × 16 matrix of byte values called an s-box.
•This matrix consists of all the possible combinations of an 8 bit sequence (28 = 16 × 16 = 256).
•However, the s-box is not just a random permutation of these values and there is a well defined method for creating the s-box tables.
•The designers of Rijndael showed how this was done unlike the s-boxes in DES for which no rationale was given. Our concern will be how state is effected in each round.
•For this particular round each byte is mapped into a new byte in the following way: the leftmost nibble of the byte is used to specify a particular row of the s-box and the rightmost nibble specifies a column.
•For example, the byte {95} (curly brackets represent hex values in FIPS PUB 197) selects row 9 column 5 which turns out to contain the value {2A}.
• This is then used to update the state matrix.
Shift Row Transformation:-
• This stage (known as Shift Rows) is shown in figure below.
• Simple permutation an nothing more.
• It works as follow: – The first row of state is not altered. – The second row is shifted 1 bytes to the left in a circular manner. – The third row is shifted 2 bytes to the left in a circular manner. – The fourth row is shifted 3 bytes to the left in a circular manner.
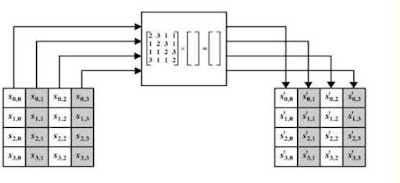
MIX COLUMN TRANSFORMATION:-
ADD ROUND KEY TRANSFORMATION:-
• In this stage (known as Add Round Key) the 128 bits of state are bitwise XORed with the 128 bits of the round key.
• The operation is viewed as a column wise operation between the 4 bytes of a state column and one word of the round key.
• This transformation is as simple as possible which helps in efficiency but it also effects every bit of state.
• The AES key expansion algorithm takes as input a 4-word key and produces a linear array of 44 words. Each round uses 4 of these words as shown in figure.
• Each word contains 32 bytes which means each subkey is 128 bits long. Figure 7 show pseudocode for generating the expanded key from the actual key.







1 Comments
good explanation
ReplyDelete