X.800 Security Attacks:-
There are two types of Software attacks:
- Active Attacks
- Passive Attacks
Active Attacks:-
An active attack attempts to alter system resources or affect their operation. Active attacks Involve some modification of the data stream or the creation of a false stream.
Active attacks are difficult to prevent because of the wide variety of potential physical, software, and network vulnerabilities. Goal is to detect attacks and to recover from any disruption or delays caused by them
• Active attacks can be subdivided into four categories:
a) Masquerade.
b) Replay.
c) Modification of messages.
d) Denial of service.
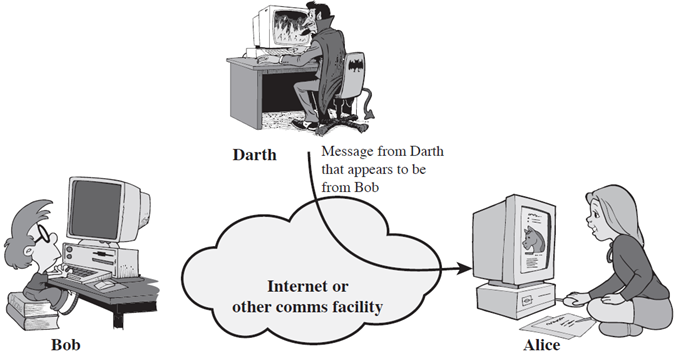
Masquerade:-
A masquerade takes place when one entity pretends to be a different entity. A masquerade attack usually includes one of the other forms of active attack. For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus enabling an authorized entity with few privileges to obtain extra privileges by impersonating an entity that has those privileges.
Replay:-
Replay involves the
passive capture of a data unit and its subsequent retransmission to produce an
unauthorized effect.
Modification of messages:-
Modification of messages simply means that some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect. For example, a message meaning “Allow John Smith to read confidential file accounts” is modified to mean “Allow Fred Brown to read confidential file accounts.”
Denial of service:-
The denial of service prevents or inhibits the normal use or management of communications facilities. This attack may have a specific target; for example, an entity may suppress all messages directed to a particular destination (e.g., the security audit service).Another form of service denial is the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance.
Passive Attacks:-
A passive attack attempts to learn or make use of
information from the system but does not affect system resources.
Passive attacks are in the nature of eavesdropping on, or monitoring of, transmissions. The goal of the opponent is to obtain information that is being transmitted.
Two types of passive attacks are:
•
a) Release of message contents.
•
b) Traffic analysis.
Release of message contents:-
The release of message contents is easily understood. A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information. We would like to prevent an opponent from learning the contents of these transmissions.
Traffic analysis:-
A second type of passive attack, traffic analysis, is
subtler. Suppose that we had a way of masking the contents of messages or other
information traffic so that opponents, even if they captured the message, could
not extract the information from the message. The common technique for masking
contents is encryption. If we had encryption protection in place, an opponent
might still be able to observe the pattern of these messages. The opponent
could determine the location and identity of communicating hosts and could
observe the frequency and length of messages being exchanged. This information
might be useful in guessing the nature of the communication that was taking
place.
Active Attacks |
Passive Attacks |
|
Data modification |
Data monitoring |
|
Affect the System |
Does not affect the system |
|
Easy to detect |
Difficult to detect |
|
Attacks on availability and integrity |
Attacks on confidentiality |
|
Examples:
|
Examples:
|
|
Techniques to avoid:
|
Techniques to avoid:
|








0 Comments